When we talk about cyber security risk, most people first think of large-scale, targeted hacker attacks on large companies and states. There is talk of Advanced Persistent Threats (APTs) - of zero-day vulnerabilities, spear phishing and CEO fraud.
In fact, cyber security here simply means that the risk is not limited to IT, but affects the entire company and originates in the cyber domain, i.e., primarily on the Internet. Thus, every small and medium-sized enterprise (SME) also exposes itself to significant cyber security risk on a daily basis, simply by having systems and employing people that interact with the Internet. However, the greatest risk to these businesses is not (nation-state motivated) targeted attacks with unknown vulnerabilities, but global malware, phishing, and ransomware campaigns by for-profit cybercriminals. These use simple scams and known vulnerabilities to inflict damage and extort money quickly and on a large scale.
The impact can be devastating. The damage of a malware or ransomware attack is often existentially threatening for small, but also for medium-sized companies. It is therefore essential for every decision-maker in a company to know what risk their employees and resources are exposed to and what options are available to effectively reduce it.
Assess cyber security risk quickly and effectively
The first and most important step is to analyze the threats and challenges to cyber security. Security frameworks can enable systematic recording, but are often, such as the BSI's IT-Grundschutz in Germany, not manageable for SMEs in terms of scope. With the CIS Controls, the Center for Information Security (CIS) provides a framework whose scope can also be geared to small and medium-sized enterprises.
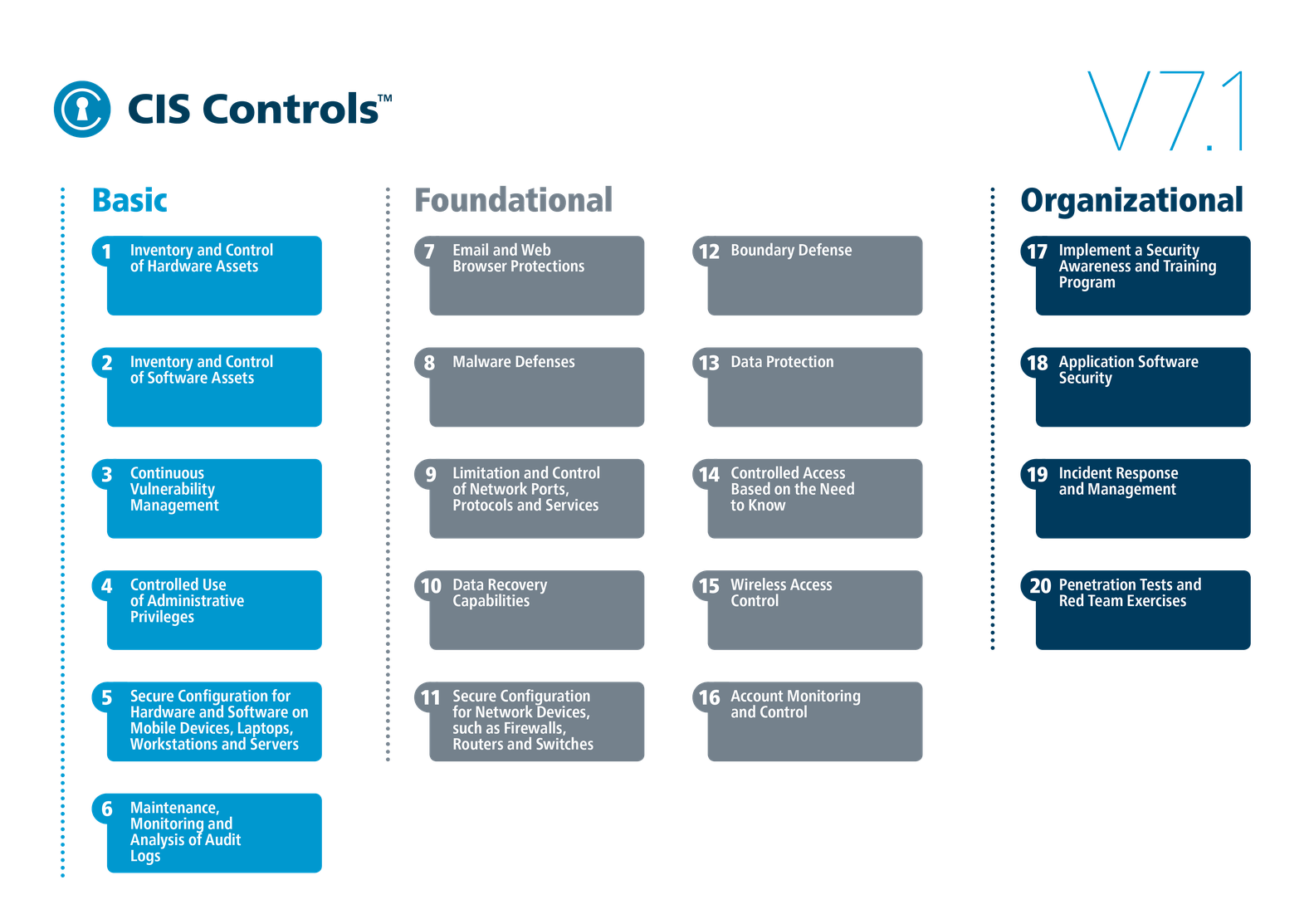
The 20 critical control points
The 20 critical control points of the CIS Controls Framework are divided into three categories:
-
The Basic category contains basic control points for managing hardware and software, as well as for authorization, configuration and vulnerability management.
-
The Foundational category houses important defenses for data, software, firewalls, routers, switches, and mobile and stationary endpoints.
-
The Organizational category deals with organizational measures such as awareness training, incident response and the execution of penetration tests.
Quelle: CIS, Lizenz: CC-BY-SA 4.0.
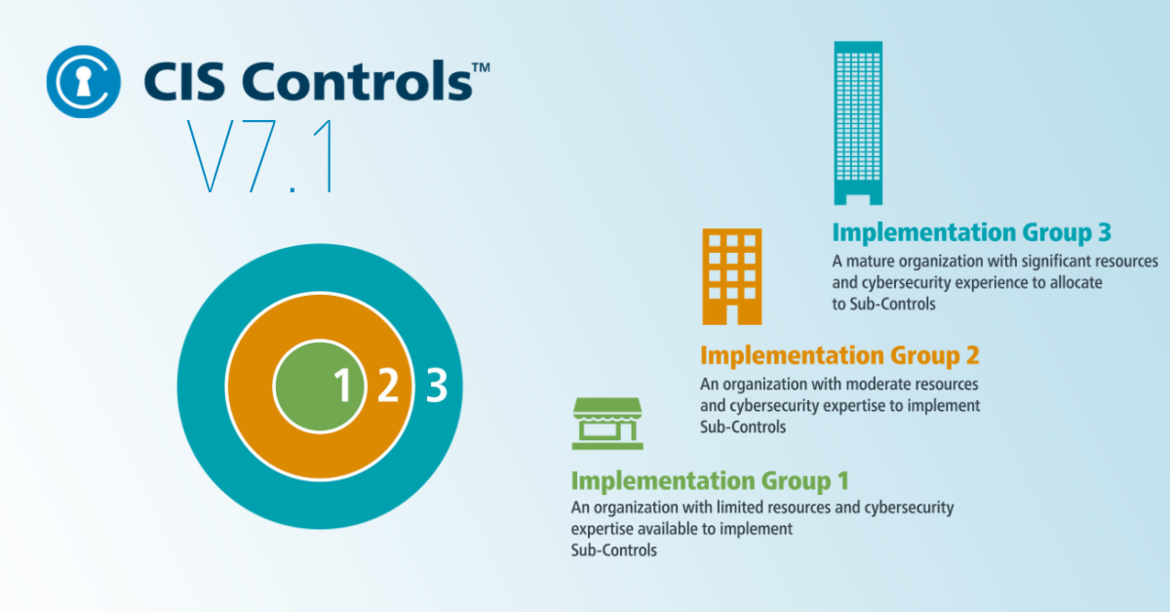
The first group, IG1, contains solutions for companies with few resources and little experience in the area of cyber security. The aim here is to create an appropriate basic level of control capabilities on which further controls and measures can be built.
IG2 contains controls for medium-sized companies and companies that have already taken measures and gained experience in the area of cyber security. Here, the focus is on efficient and pragmatic protection against malware, phishing and ransomware, among other things.
Finally, IG3 is for companies that have sufficient expertise and resources to arm themselves against the APTs and zero-day hacks mentioned at the beginning.
In practice, this looks like this: In order to use Control Number 6 Maintenance, Monitoring and Analysis of Audit Logs to ensure that the necessary log files are available for post-mortem analysis after an IT incident, IG1 requires that the audit logs of all relevant systems be activated. This usually generates only one-time effort. In IG2, centralized log management with analysis capabilities is to be introduced so that security personnel can quickly identify new threats such as a malware infection or a DDoS attack and track them retroactively. Finally, to protect large infrastructures and also detect novel attacks with zero-day vulnerabilities, IG3 will consolidate information into a SIEM and partially automate response.
For companies of all sizes, the Implementation Groups also provide a good guide for prioritizing security measures. This ensures that core issues are addressed first, optimally reducing cyber security risk from the outset. More information on the Implementation Groups can be found in the associated CIS whitepaper.
Do the check yourself now
For anyone who wants a quick overview of their current cyber security situation, CIS offers the so-called CIS Controls Self-Assessment Tool (CSAT). With the free tool, theoretically anyone who has the necessary overview of the measures currently implemented can perform a cyber risk assessment.
The CIS Controls provide a quick and effective entry point to cyber security risk analysis. However, anyone who runs the CSAT and takes a look at the sub-controls will notice: it is not an "out-of-the-box" checklist. For each checkpoint, the generically formulated requirement must be adapted to the technological and organizational circumstances of the company's IT and, if necessary, inappropriate requirements must be revised or replaced appropriately.
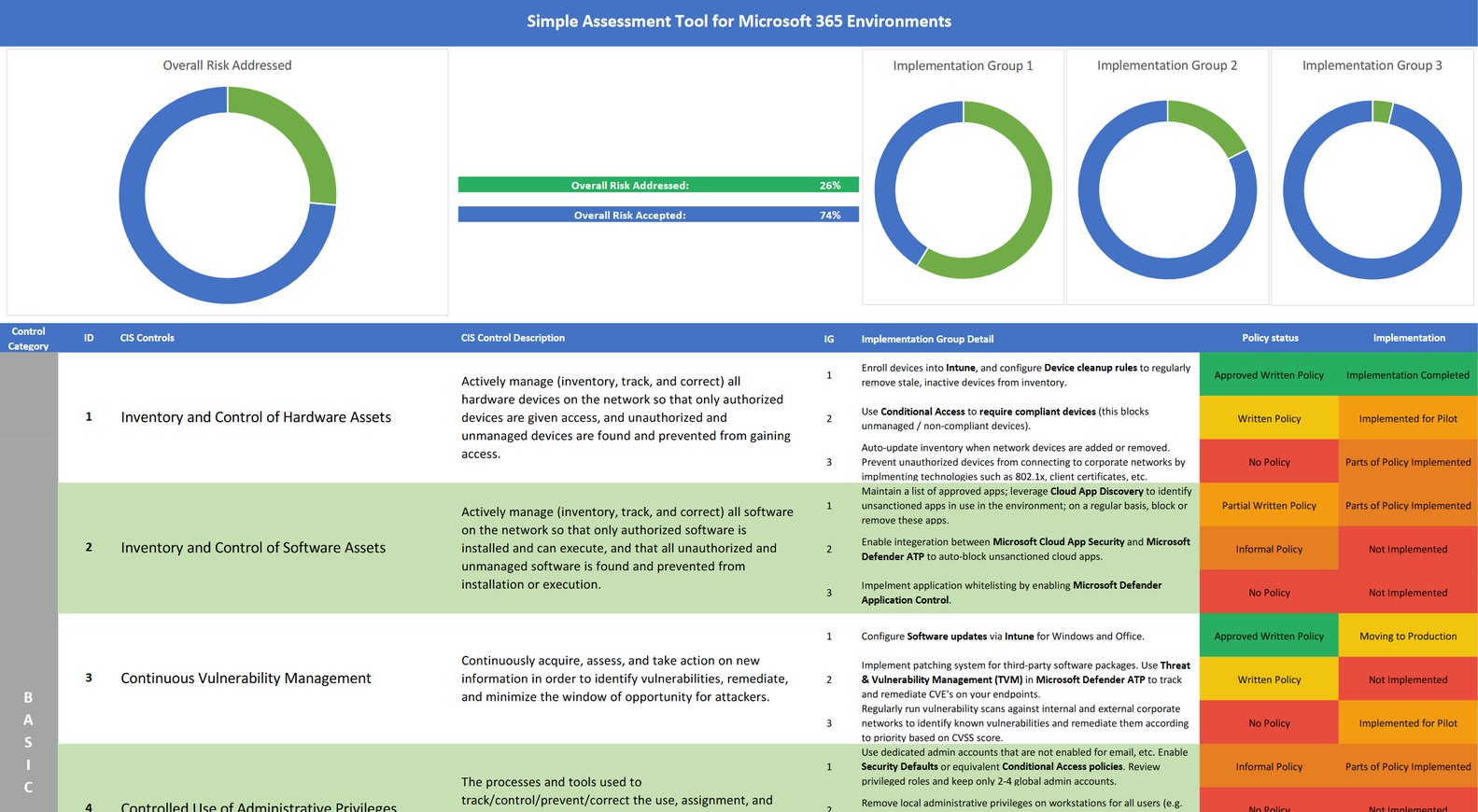
Our cyber security analysis for Microsoft 365 customers
Especially companies that have made the leap to the Microsoft cloud actually already have all the technological prerequisites to implement the basic control points of Implementation Groups 1 and 2. However, they usually lack the expertise and the guidelines with which the objectives of the controls can then also be achieved.
For example, the sub-controls in IG1 call for the ongoing inventory of all hardware, as well as selective release of software, in IG2 a tracking of actually installed software, and in IG3 an integration that brings this information together. All three controls are technologically covered by the use of Microsoft Intune for their end devices. However, it must also be operationally ensured that all devices are included and a software blacklist or whitelist is maintained and enforced!
We therefore offer a cyber security analysis fully customized to the Microsoft 365 cloud offering. With our questionnaire on the implementation status and usage behavior of the various Microsoft security tools such as Microsoft Intune, Microsoft Information Protection or Azure AD Security Defaults, you can thus clearly visualize your addressed and unaddressed risks and use them to develop a concrete action plan for your company's cyber security strategy in discussion with us.
Conclusion: Making risks & opportunities visible quickly
The CIS Controls also offer small and medium-sized companies the opportunity to quickly assess their cyber security risk and identify opportunities for improvement through generic measures.
Our cyber security analysis also gives you the opportunity to show the concrete implementation status of technological measures in Microsoft 365 and to clearly visualize the cyber security risk addressed as a result.
Learn more about our IT security consulting here.
![[Translate to English:] Cyber Security für KMUs [Translate to English:] IT Security Bildschirm](/fileadmin/_processed_/5/e/csm_Cybersecurity_4a19defb9f.jpg)